Silk Road 2 Seized: FBI Report Highlights
Posted on November 08, 2014 in Blog • 3 min read
It is not a flashing news, yesterday Silk Road 2 has been closed, admin has been arrested and charged, meanwhile in US and EU servers have been seized by various law enforcement agencies.
The operation dubbed “Onymous” was a joint effort of FBI, Eurpol, Eurojust and US Homeland Security, it was publicly advertised on FBI’s twitter profile.
Many good articles are available about operation details and Silk Road admin profile so I don’t want to duplicate them, just have a look to these nice reads:
- Silk Road 2 Seized! (Multiple Markets Seized)
- Feds Arrest Alleged ‘Silk Road 2′ Admin, Seize Servers
The interesting point is the published sealed complaint, a 33-pages document full of details. It teach us something about OPSEC and Silk Road operation.
I suggest you to have a look over the document, there are some interesting highlights:
The Silk Road 2 admin, Blake Benthall aka “Defcon” is not alone, there are others known and unknown people involved. So this one could not be the only arrest.
He is accused of: narcotics trafficking conspiracy, conspiracy to commit and aid and abet computer hacking, conspiracy to transfer fraudulent identification documents, money laundering conspiracy.
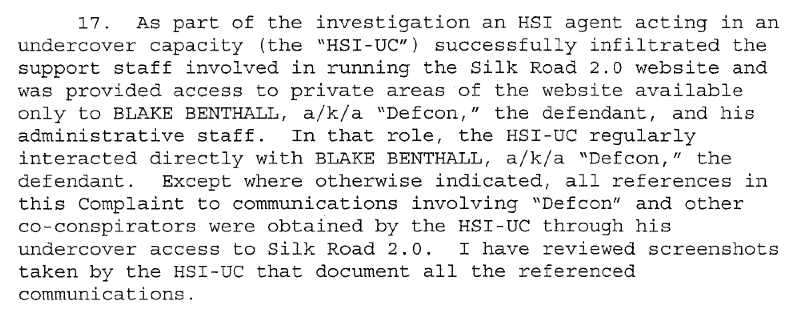
An undercover US Homeland Security agent infiltrated inside the support forum stuff and gained access to private areas. The agents are used to get screenshots as proof.
FBI estimated Silk Road 2 was generating sales of at least 8$ million and 400.000$ in commissions in October 2014.
FBI places the born of Silk Road 2 on 6th November 2013.
The site was an shopping mall for drugs and illegal services, just click on an item and put it in the shopping cart, probably the most known feature of Silk Road ever. The website had almost the same features of Silk Road 1.
The admin implemented a Bitcoin tumbler, like in Silk Road first release.
The fee was generally from four to eight percent, after a while a fixed fee of five percent was fixed for all services.
On December 2013 the admin posted a message saying “DPR places operational security above all else”. Sorry if I tell you, this is an OPSEC fail.
The admin promptly moved the servers hosting Silk Road 2 when the Tor Project announced the Tor’s “de-anonymity” vulnerability. That is real vulnerability response.
The admin was aware of “business” risks.
On September 10, 2014 someone around 1,5$ million were stolen by someone.
The website had approximately 150.000 monthly active users.
The admin tried to recruit large scale narcotics vendors. He was really marketing oriented, he focused on how to grow the vender user base, improve the offer with new products and how to be competitive in the market.
Some kind of intelligence was available to website stuff: they warned Minnesota’s users about an FBI operation defined as “large darknet related operation”.
The admin stated in a forum’s message that protecting website infrastructure and servers from being seized by law enforcement was him top priority. Fail.
Law enforcement put offline a server and imaged it, a forensic analysis was performed. They extracted private keys to run Tor hidden server and the website, chat logs and server configuration.
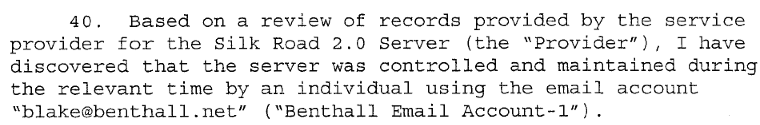
Blake used his personal email to lease, control and maintain the server.
Blake accessed email with his original IP address, easily tracked to his hotel room.
Blake was active on social networking sites (Twitter, Github) and leaked some information.
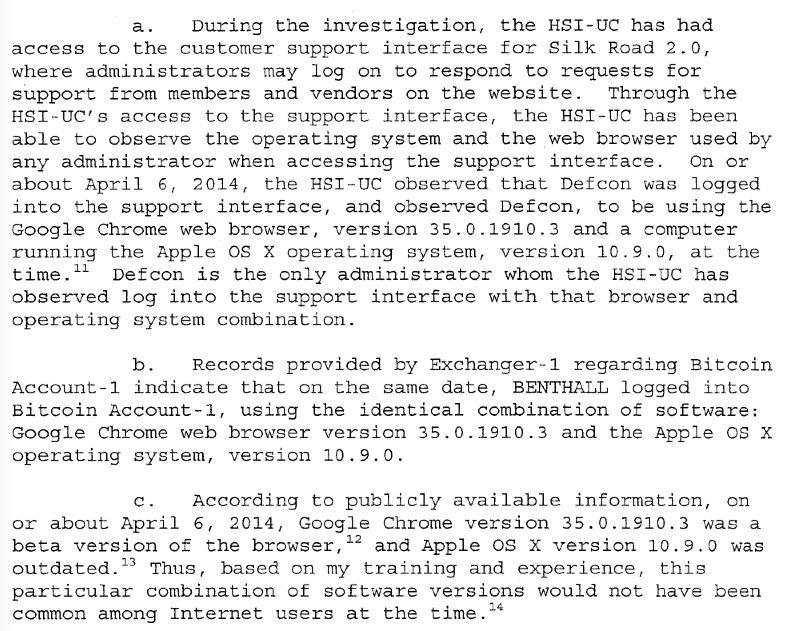
Browser fingerprint was used as a proof to identify Blake.
Long story short: Silk Road 2 admin did a good job but it was not enough. He failed in some points about about OPSEC in a job where you can’t fail.
Kudos to FBI and other agencies for the joint operation.